A few weeks ago we added Cloudflare SSL support for blogs hosted on EBN. While in the process of integrating CloudFlare we did thorough research on potential leaks and footprints. Here are our findings.
Is CloudFlare successfully masking my server’s real IP?

In essence, if you know exactly what you are doing and are very careful, then using Cloudflare to mask your PBN’s IPs is OK. But in reality, a lot of people have misconfigured PBNs and it is rather easy to get the real IPs they are using.
It’s still way easier to use properly configured PBN hosting like Easy Blog Networks.
If you still want to use a single (or a small number of) server for your entire PBN and mask it with Cloudflare, you need to be careful with the following:
1. Cloudflare nameservers footprint
Problem: Cloudflare has over 100 nameservers, but when you sign up with Cloudflare your account is assigned only two of them. If you put your entire PBN on these two nameservers, you created a footprint, since only a small fraction of sites have exactly your combination of nameservers (out of a total of over 1500 combinations).
Solution: For every blog, create a separate Cloudflare account.
2. Misconfigured zonefile
Problem: By default, Cloudflare adds a “direct connect“ subdomain to the zone file when you add a site. This allows you to access your site directly in case something goes wrong with Cloudflare configuration. The problem is that this also reveals the real IP of your site
Solution: Login to Cloudflare and remove any “direct connect” subdomains.

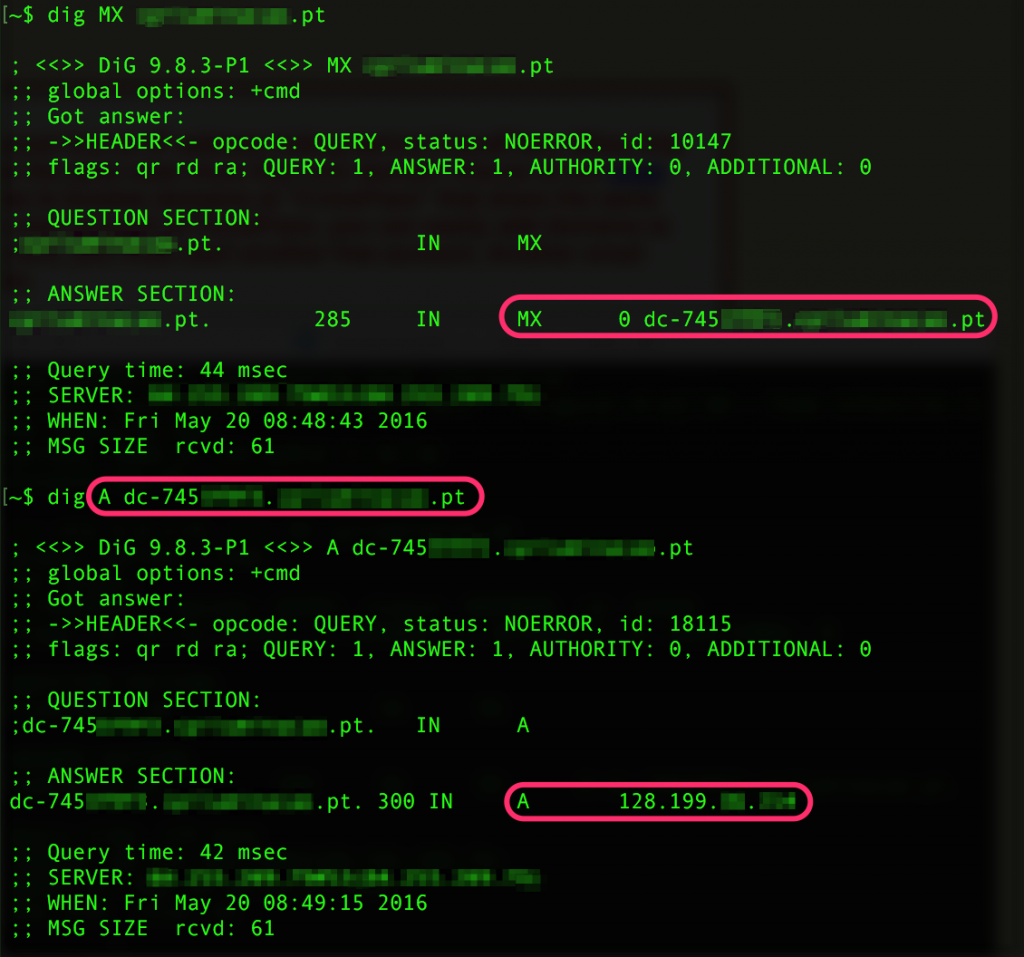
3. MX records
Problem: In our previous post we showed that it is important to have MX records set on the majority of your PBNs. However, Cloudflare does not support shadowing emails so your MX records point to the real IP of your site.
Solution: Use a third-party email provider, such as Rackspace Email.
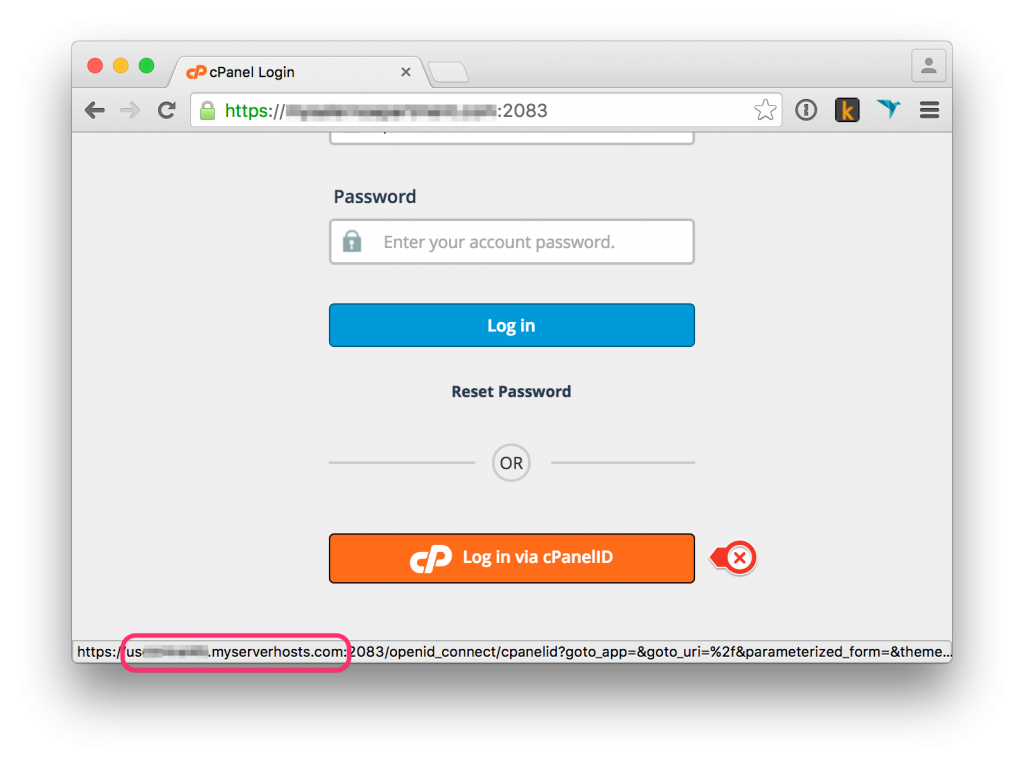
4. cPanel leaks
Problem: cPanel, by default, uses cPanelID authentication scheme. This leaks the server’s IP as it redirects you to the server’s subdomain to perform the authentication. It is easy to get the server’s IP from its subdomain and your PBN is revealed.
Solution: Do not use hosts with cPanel.
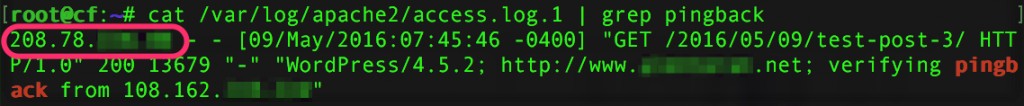
6. WordPress Pingbacks
Problem: By default WordPress supports pingbacks. Under the hood, pingbacks tell your blog to send a pingback confirmation request to the blog that sent the pingback. This means a malicious person can deploy a blog on his or her server, then pingback your blog, and your blog will send a request to the malicious person’s blog. Looking at Apache logs it is easy to see your blog’s real IP.
This applies to other similar techniques, such as using embed in comments, etc. Whatever outbound traffic your blog sends out, does not go through Cloudflare and will leak your real IP.
Solution: Disable pingbacks and comments, be *very* careful what plugins you install. To be safe also disable registration and do not send any emails out from your blog.
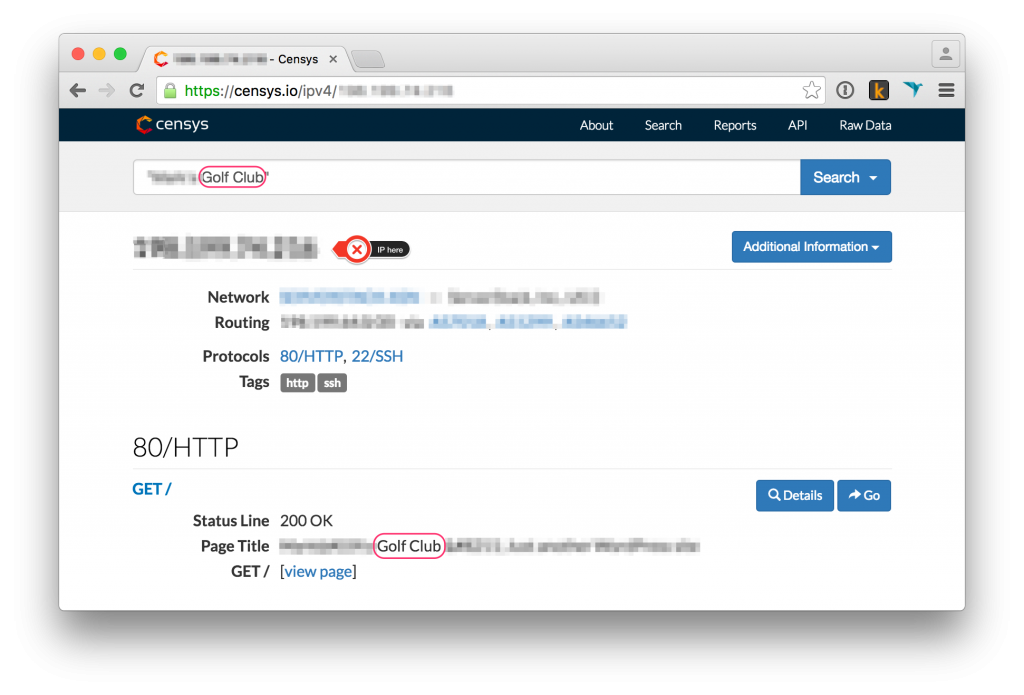
6. Server default page
Problem: By default, some hosting providers will configure your server to serve one of your blogs as default. This means that if you enter your server’s IP in the browser, you will see one of your blogs. This is a huge problem since there are crawlers such as censys.io and shodan.io that crawl all IPs and save what they get. Then it is easy to use their search engines to search for domains returned by IPs and your default blog is in their results!
Solution: Make sure your server does not serve any relevant content as the default page.
7. The hardest problem: getting everything above right!
Problem: If you have a 20-blog PBN, with 19 blogs configured perfectly and *just one misconfigured* blog, your entire PBN is in danger. Using some command-line magic, it is easy to check whether a list of domains are hosted on a certain IP, which reveals your entire PBN that is hosted on the same server as the misconfigured blog.
Solution: Use many small servers with few deployed blogs instead of one big one. In case one blog leaks its IP, the damage will be limited. Or use EBN to deploy each of your blogs on a different server :).
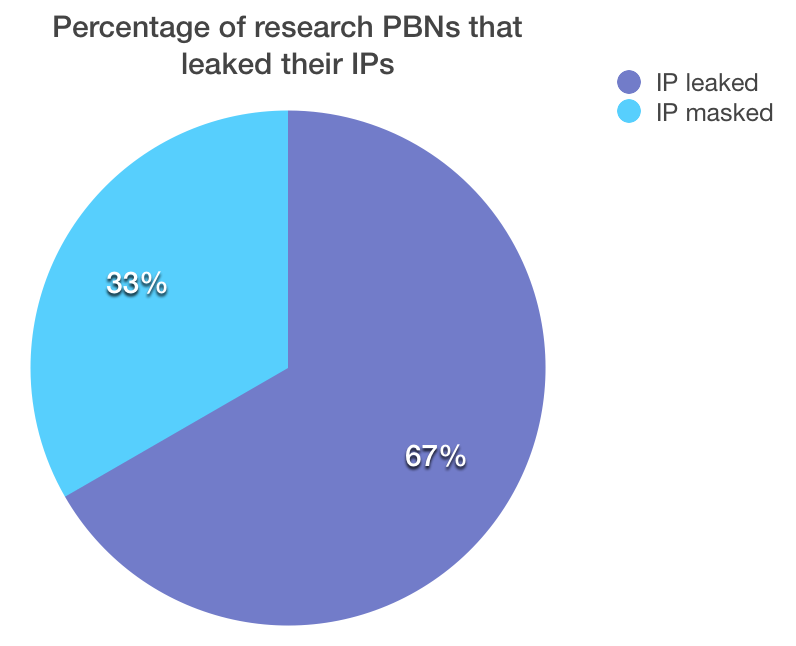
Research Results
In our research, various people sent us over 60 sites hidden behind Cloudflare. After searching for leaks described above only one-third of blogs did not leak their IPs. In other words: two-thirds of PBNs hidden behind Cloudflare that people actually use to rank their money sites are leaking their IPs! Are you absolutely sure you are among the minority that has everything configured perfectly?
Resources:
- http://tipstrickshack.blogspot.si/2012/11/how-to-find-real-ip-protected-by-cloud.html
- https://geekflare.com/find-real-ip-address-of-website-powered-by-cloudflare/
- http://iphostinfo.com/cloudflare
- http://censys.io and http://shodan.io/
P.S.: Special thanks to all the folks who helped us with the research by sending us their domains and then confirming when we got their real IP. We could not have done it without you!